Do you really need to spend on identity theft software or services? Or can you secure your identity by simply doing things that prevent identity thieves from taking and using your information? To answer this question, let’s review the following list of things you should to do to shield yourself from someone who may want to steal your identity.
Identity Theft Protection Checklist
If you aren’t actively doing 10 or more of these items, then you should probably look into subscribing to an identity protection service.
- Never share your login details with anyone. If you keep your passwords in a digital file, then make sure that the file is encrypted.
- Secure your social security number (SSN). It’s advisable to not always carry it with you. There aren’t that many instances when you have to show your SSN to anyone.
- Avoid telling anyone you are not familiar with your personal details such as your birthdate, address, age, workplace, and social media accounts. Don’t present your official ID cards to anyone unless they are required for some official purpose.
- If you still subscribe to physical mail (aka snail mail), then make sure you collect your mail every day. Your mail can contain information about you that can be used by people with felonious intentions.
- Secure your smartphone. Adopt the habit of password-protecting your device even if you think you don’t have anything critical to protect.
- Properly discard documents or materials that have your personal information. These include your expired credit cards, account statements, invoices, receipts, and contracts.
- Make sure your passwords are unpredictable. Avoid passwords and PINs that are based on your personal details such as your birthdate. Also, don’t use the same password for all of your accounts.
- Your computers and gadgets should always have anti-malware software installed on them. It also helps to have firewalls enabled.
- Regularly access or monitor your online accounts. Most online accounts come with a session tracking feature, which lets you view the history of logins to an account. This will help you check if somebody is accessing your account without your permission. If you have online accounts that you no longer use, then delete them.
- Take advantage of two-factor authentication or 2FA. This requires more than just a password to access an account. For example, you may be required to enter a transaction password (which is sent to your mobile device) in addition to entering your password to access an account.
- Use a VPN when accessing public Wi-Fi hotspots. VPNs can prevent the sniffing of the data you submit or accept while using a hotspot.
- If you don’t intend to apply for any loan or credit facility, consider freezing your credit files. You can do this for free with the help of services like Experian, Equifax, TransUnion, and the National Consumer Telecommunications and Utilities Exchange. By freezing your credit files, nobody can use your identity to apply for any credit account.
The items listed above are just a few of the things you need to do to avoid becoming the victim of identity theft. If you are committed to doing all of them meticulously, then you probably won’t need professional identity theft protection. However, if you want convenience and a stronger guarantee that your identity won’t be stolen, even in the case of a cyber attack, then you should consider professional identity protection.
Identity Theft Services: What Should You Look For?
Many identity protection services will handle everything that’s required to secure your identity. This often includes the checklist above as well as monitoring the USPS for address changes and scanning the dark web for your personal details.
Another feature to look for is if a company offers assistance in recovering your identity if necessary. This might include reimbursement clauses, compensation for personal expenses, and fees for lawyers and experts to find and litigate identity thieves.
Do You Live In A High-Risk Identity Theft Area?
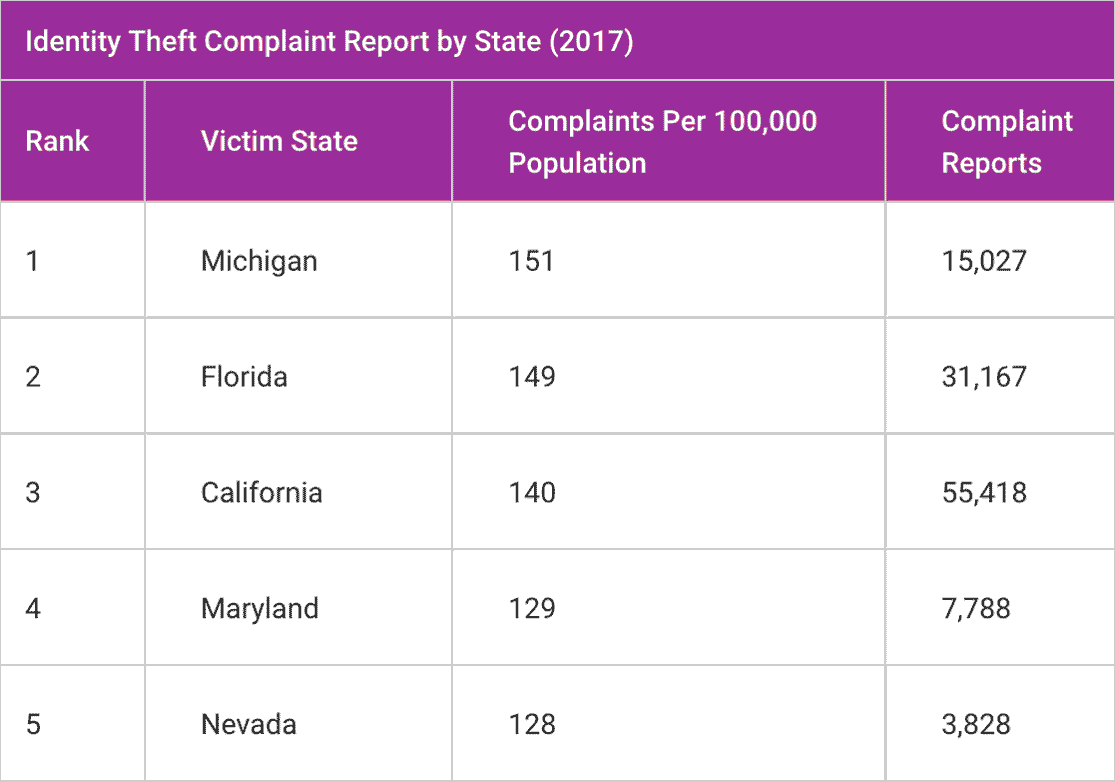
Another factor to consider when evaluating your identity protection needs is where you live. For example, residents of some US states are much more likely to fall victim to an identity attack. According to Experian, the ten states with the highest per capita rate of reported identity theft are Michigan, Florida, California, Maryland, Nevada, Delaware, Illinois, Rhode Island, Georgia, and Arizona.
Budgeting For Identity Protection
Getting identity theft protection software or a service plan is a good idea, especially if it’s within your means. Subscribing to identity protection services or identity protection software often isn’t cheap, especially for plans that provide comprehensive coverage. However, if you being targeted for identity theft attacks, then it’s worth the money and extra peace of mind. Stay safe out there.
Related Articles:
- Jimmy Kimmel Demonstrates How To Social Engineer Passwords
- How To Secure Your Data From WiFi Hacking Attacks
- StP-II Test Can Predict How Likely You Are to Fall for An Internet Scam
- Snoops, Beware: Man Faces Jail Time For Breaking Into His Wife’s Email

Private investor. Tech enthusiast. Broadcast TV veteran.






















 6 of the Funniest Parody Films Ever Made
6 of the Funniest Parody Films Ever Made
Leave a Reply