Has someone been using your computer without your permission or attempting to guess your password? The Macintosh app, Digital Sentry, monitors your computer for specific events, like an incorrect password, and then can perform a vast array of unique actions in response.
Monitors & Actions
When Digital Sentry monitors a suspicious action, like a wrong password attempt or IP address change, then it can execute recipes of actions like sending a secret e-mail, shutting down your computer, pinging a URL, taking a photo or screenshot, playing a multimedia file, speaking some text, executing a shell script and much more.
In the screenshot below you can see examples of some of the possible monitors in Digital Sentry including the amount of time passes, power source changed, a key was pressed and IP address changes.
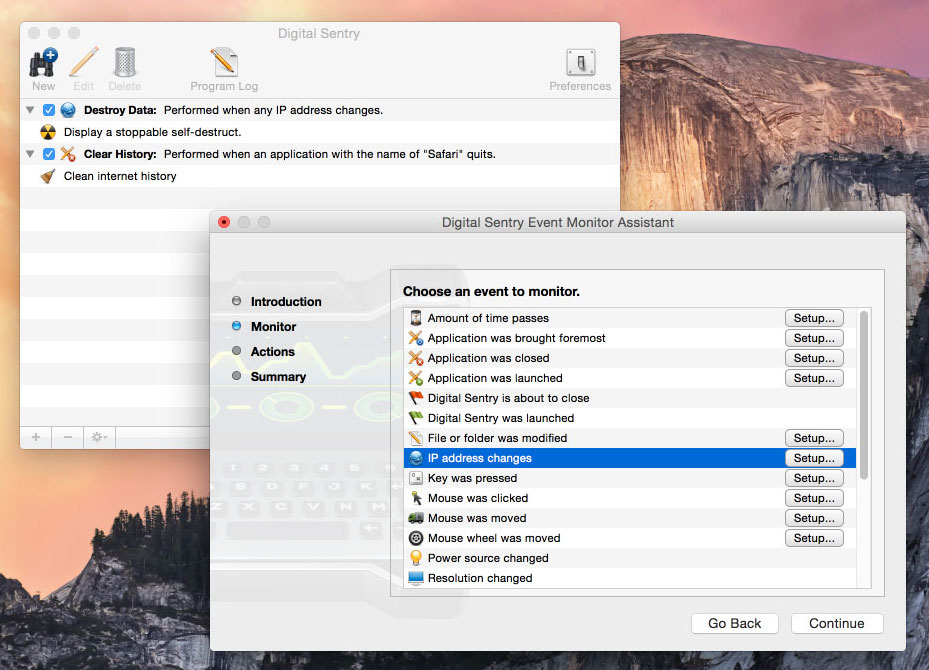
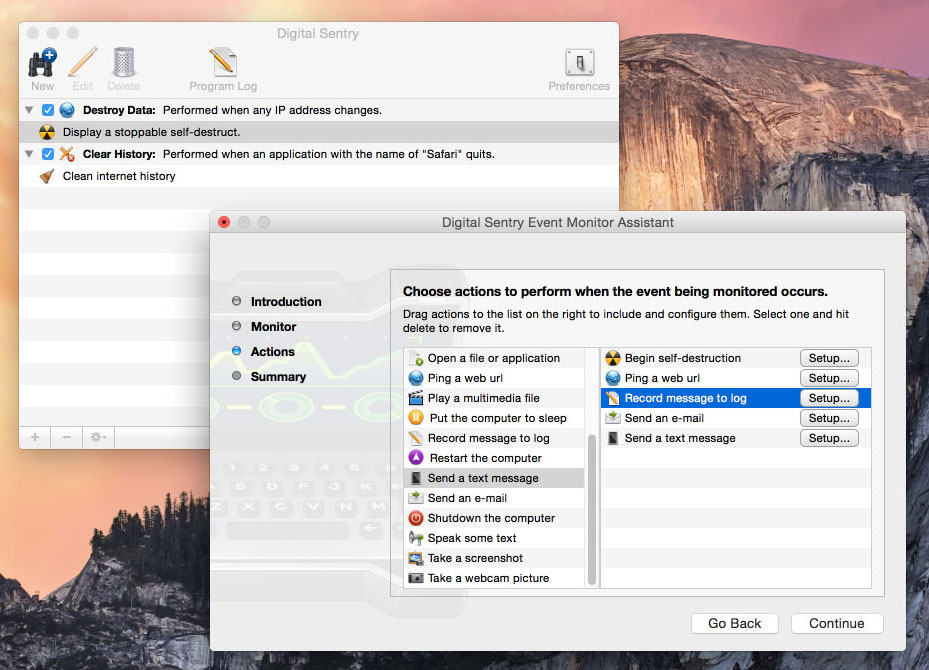
And here are some examples of the actions you can perform:
- send a text message
- play a multimedia file
- restart the computer
- shut down the computer
- take a webcam picture
- take a screenshot
All of these actions enable you to get very creative. Combining them in unique ways can make for some fun pranks. And will also allow you to bust the person messing with your computer.
Simulating a Self-Destruct Sequence
You know in the movies when someone tries to access a hacker’s computer and then it initiates a self-destruct? For example, the movie Robot & Frank.
Digital Sentry can’t actually blow-up your computer. But you can combine a series of actions like playing a video like this Star Trek self-destruct sequence below, and then shut down your computer every time it monitors something like a wrong password being entered.
Keeping Friends & Family Away From Your Computer
I hate it when someone uses my computer. Use your own laptop damn it. I first found out about Digital Sentry after I busted my ex-girlfriend using my laptop. I saw some webcam photos of her with her girlfriend on my computer and confronted her about it. She took my laptop to her friend’s house. My laptop has all of my banking info and personal files on it. I don’t want it leaving my apartment without my permission.
Digital Sentry also helped me permanently stop my old roommate from touching my Mac. If someone knows that every action they perform, every keystroke and every moment is captured and logged, then they tend to stay away.
Digital Sentry: Free Trial
 Koingo Software‘s Digital Sentry has a 15-day free trial and is definitely worth checking out. It’s an ideal solution for catching a thief in the event your laptop has been stolen. For only $19.95, it’s an incredible tool for performing covert surveillance and protecting your data during unauthorized access or theft.
Koingo Software‘s Digital Sentry has a 15-day free trial and is definitely worth checking out. It’s an ideal solution for catching a thief in the event your laptop has been stolen. For only $19.95, it’s an incredible tool for performing covert surveillance and protecting your data during unauthorized access or theft.

Frank Wilson is a retired teacher with over 30 years of combined experience in the education, small business technology, and real estate business. He now blogs as a hobby and spends most days tinkering with old computers. Wilson is passionate about tech, enjoys fishing, and loves drinking beer.






























 How To Uninstall Spyware and Adware from Mac OS X
How To Uninstall Spyware and Adware from Mac OS X
Leave a Reply