The Internet-of-Things (IoT) is all around us. Our homes, our offices, and even our cars are slowly being accessorized by Internet-connected devices. A decade ago, the connected devices in your home were probably limited to just computers and phones. Now everything from security cameras, voice assistants like Alexa, toys and even light bulbs have Internet access. Here’s how the Dyn DDoS attack caused havoc around the world.
Table of Contents[Hide][Show]
Impact Of The Dyn DDoS Attack
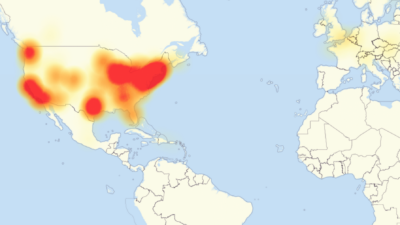
But with the new connectivity comes new opportunities for hackers. In October 2016, a massive Distributed Denial of Service (DDoS) attack on an Internet infrastructure company called Dyn affected many devices and companies around the world. Hackers were able to gain access to millions of IoT devices around the world. These devices then all sent false requests to Dyn at the same time.
The short-term result of the hack was the temporary shutdown of many popular websites including Netflix, Twitter, Spotify, and LinkedIn. But the hack created a bigger problem for companies like Chinese electronics maker Hangzhou Xiongmai Technology. The hack forced them to issue a security patch for their devices made before April 2015 and recall 10,000 of its webcams. The recall included products dating back to 2014, and the company confirmed that it has improved its security since then, making precautions like blocking remote Telnet access to IoT devices.
Software and app developers were also impacted by the hack. They need to be more proactive about the security of their users.
“The recent Dyn DDoS attack… is just the tip of the IoT security iceberg,” said Arxan CMO Mandeep Khera, “and we’ll likely see more large-scale IoT attacks in the next year.” Arxan is an American technology company specializing in application attack prevention.
Securing Smartphones
As more devices become connected in 2017, both businesses and consumers will need to take precautions to keep their smartphones protected. Our phones often hold the key to accessing other technologies. Always check the publisher’s name in the app store, and research developers of apps whose names you don’t recognize before downloading an app.

Communication channels that make it easy to use controls hands-free in cars also expose the electronic control units to a number of risks for automotive IoT. This could potentially include allowing hackers access to the OBD2 port through exploiting channels the port uses to communicate with the engine.
Using A VPN
One simple way both businesses and consumers can help protect themselves when accessing the Internet is by using a VPN. Virtual private network (VPN) software can be installed on both smartphones and computers and provide an extra layer of security. A VPN routes all traffic through their secure servers before connecting to the Internet. Using a trusted VPN, like NordVPN, prevents hackers who might be sniffing traffic on public networks from capturing your data.
Cyber Extortion Concerns
The growth rate of cyber extortion is extremely alarming. In 2015, the total ransom paid by businesses amounted to just 11% of the extortion money paid for hackers to unlock frozen data in 2016.
With such a major year-over-year increase, many businesses may need to rethink administrator access privileges. The FBI recommends a centralized patch management system for servers. This will allows companies to send out updates to multiple parts of their infrastructure. This will work even if these components run on different operating systems and hardware.

Frank Wilson is a retired teacher with over 30 years of combined experience in the education, small business technology, and real estate business. He now blogs as a hobby and spends most days tinkering with old computers. Wilson is passionate about tech, enjoys fishing, and loves drinking beer.




















 Smart Thief Steals 42 Inch TV With Style
Smart Thief Steals 42 Inch TV With Style
i wonder if my security system at home was hacked. how do i find out?
it probably was. you should call them and ask about a firmware update.